Information Security Program Guide For State Agencies
Publication 1075 tax information security guidelines for federal state and local agencies safeguards for protecting federal tax returns and return information. Deceased persons visa records continue to be protected under the visa confidentiality provisions of ina section 222f even after the subject is deceased. Mark egans 2004 the executive guide to information security is as promised an executive guide written in laymans language for planning and executing information security policy in a corporate environment. Read the notice of proposed rulemaking to help small businesses strengthen retirement security in america. Interagency guidelines establishing information security standards introduction important terms used in the security guidelines developing and implementing an information security program.

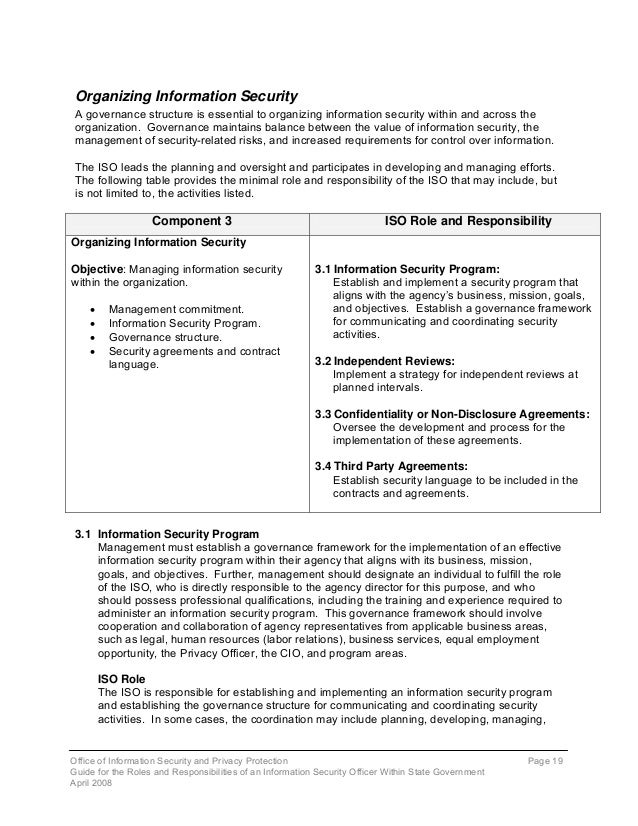
The Information Security Program Guide was originally developed by a workgroup of state agency Information Security Officers (ISO) in March 2006 as a guide to assist agencies in developing an information security program or enhancing their existing program. Office of Information Security and Privacy Protection. Information Security Program Guide for State Agencies. April 2008 (Version 3). Table of Contents. The mission of the Information Security Program Audit (ISPA) team is to provide. And procedures are accessible online in the State Administrative Manual (SAM). Contain compliance information that is customized to the agency audit scope.
Information Security Program Basic Security Advanced Security Information Security Program This Information Security Handbook provides a broad overview of information security program elements to assist managers in understanding how to establish and implement an information security program. The purpose of this publication is to inform members of the information security management team agency heads, chief information officers (CIO), senior agency information security officers (SAISO), and security managers about various aspects of information security that they will be expected to implement and oversee in their respective organizations. This handbook summarizes and augments a number of existing National Institute of Standards and Technology (NIST) standard and guidance documents and provides additional information on related topics. This handbook is a guide to developing computer security policies and procedures for sites that have systems on the Internet.
The purpose of this handbook is to provide practical guidance to administrators trying to secure their information and services. The subjects covered include policy content and formation, a broad range of technical system and network security topics, and security incident response. The SANS Top 20 is a consensus list of vulnerabilities that require immediate remediation. It is the result of a process that brought together dozens of leading security experts. They come from the most security-conscious government agencies in the UK, US, and Singapore; the leading security software vendors and consulting firms; the top university-based security programs; the Internet Storm Center, and many other user organizations.
SCORE is a cooperative effort between SANS/GIAC and the Center for Internet Security(CIS). SCORE is a community of security professionals from a wide range of organizations and backgrounds working to develop consensus regarding minimum standards and best practice information, essentially acting as the research engine for CIS. After consensus is reached and best practice recommendations are validated, they may be formalized by CIS as best practice and minimum standards benchmarks for general use by industry at large. Use of the NSA IA-CMM increases an organization’s capability to provide ongoing support and confidence that its technical work force is performing according to an established and mature INFOSEC Assurance process. The goal is to gain relative assurance that the INFOSEC Assurance process is consistent and repeatable over time. The OWASP Top Ten is becoming the defacto standard for web application security.
Federal Trade Commission strongly recommends that all companies use the OWASP Top Ten and ensure that their partners do the same. In addition, the U.S. Defense Information Systems Agency has listed the OWASP Top Ten as key best practices that should be used as part of the DOD Information Technology Security Certification and Accreditation (C&A) Process (DITSCAP). The original OWASP Guide to Building Secure Web Applications has become a staple diet for many web security professionals. Over the last 24 months the initial version has now been downloaded over 2 million times.
The Guide forms the basis for corporate web security policies for several Fortune 500 companies and is used in service offerings from many security consulting companies. The Guide is aimed at architects, developers, consultants and auditors and is a comprehensive manual for designing, developing and deploying secure web applications. The overall purpose of the International CIIP Handbook 2004 is to provide an overview of CII protection practices in several countries.
The book investigates two main questions: 1) What national approaches are there to CIIP? And 2) What methods and models are used in the countries surveyed in order to analyze and evaluate various aspects of CII? The handbook’s target group consists mainly of security policy analysts, researchers, and practitioners. The handbook can be used either as a reference work for a quick overview of the state of the art in CIIP policy formulation and CIIP methods and models or as a starting point for in-depth research. Whether your organization is large or small, a thorough, detailed information security plan should be part of your security formula.
This article provides some useful information on implementing a viable plan that not only complies with government regulations, but also eliminates costly threats. GAISP’s goal is to collect information security principles that have been proven in practice and accepted by practitioners, and to document those principles in a single repository – hence the name, Generally Accepted Information Security Principles.
GAISP draws upon established security guidance and standards to create comprehensive, objective guidance for information security professionals, organizations, governments, and users. This technical report is a survey of existing techniques which could potentially be used in the analysis of security architectures. The report has been structured to section the analysis process over three broad phases: the capture of a specific architecture in a suitable representation, discovering attacks on the captured architecture, and then assessing and comparing different security architectures.
Each technique presented in this report has been recognised as being potentially useful for one phase of the analysis. Information Security Control Frameworks COBIT has been developed as a generally applicable and accepted standard for good Information Technology (IT) security and control practices that provides a reference framework for management, users, and IS audit, control and security practitioners. This document issued by the ITGI reflects the latest thinking on this increasingly global topic. Based on COBIT control objectives, the authors have designed this publication as an educational resource primarily for IT control professionals, but CIOs, IT management and assurance professionals will find the information vitally important and beneficial as well. The purpose of this publication is to provide guidelines for selecting and specifying security controls for information systems supporting the executive agencies of the federal government. The guidelines apply to all components5 of an information system that process, store, or transmit federal information.
When you want to save money and do the job right the first time, turn to an online Chilton Hyundai Accent repair manual. Accent repair manual.
'This document aims to meet the needs of executives and managers who are accountable for the security of information assets; staff who are responsible for initiating, implementing and or monitoring risk management within their agency; and staff who are responsible for initiating, implementing and or maintaining information security within their agency.' The Common Criteria defines a language for defining and evaluating information technology security systems and products. The framework provided by the Common Criteria allows government agencies and other groups to define sets of specific functional and assurance requirements, called protection profiles. Information Security Standards ISO 27002 is intended to serve as a single reference point for identifying the range of controls needed for most situations where information systems are used in industry and commerce, and to be used by large, medium and small organizations. This standard was approved by the Securities and Exchange Commission on June 17, 2004, and is effective for audits of internal control over financial reporting required by Section 404(b) of the Sarbanes-Oxley Act of 2002.
Staffing Agencies For Security Positions
Information Security Legislation HIPAA provides the first comprehensive Federal protection for the privacy of health information. The Sarbanes-Oxley Act mandates a number of reforms to enhance corporate responsibility, enhance financial disclosures and combat corporate and accounting fraud, and created the 'Public Company Accounting Oversight Board,' also known as the PCAOB, to oversee the activities of the auditing profession. The Gramm-Leach-Bliley Act includes provisions to protect consumers personal financial information held by financial institutions. Copyright © 2003 - 2008 - USSecurityAwareness.org - All rights reserved.